MP4Box 无限循环漏洞
0x00 前言
漏洞软件地址:
0x01 漏洞挖掘
AFL++:
./configure --static-bin
0x02 漏洞分析
gdb调试crash文件,触发命令为MP4Box -v -fstat <crashfile>。
堆栈如下:
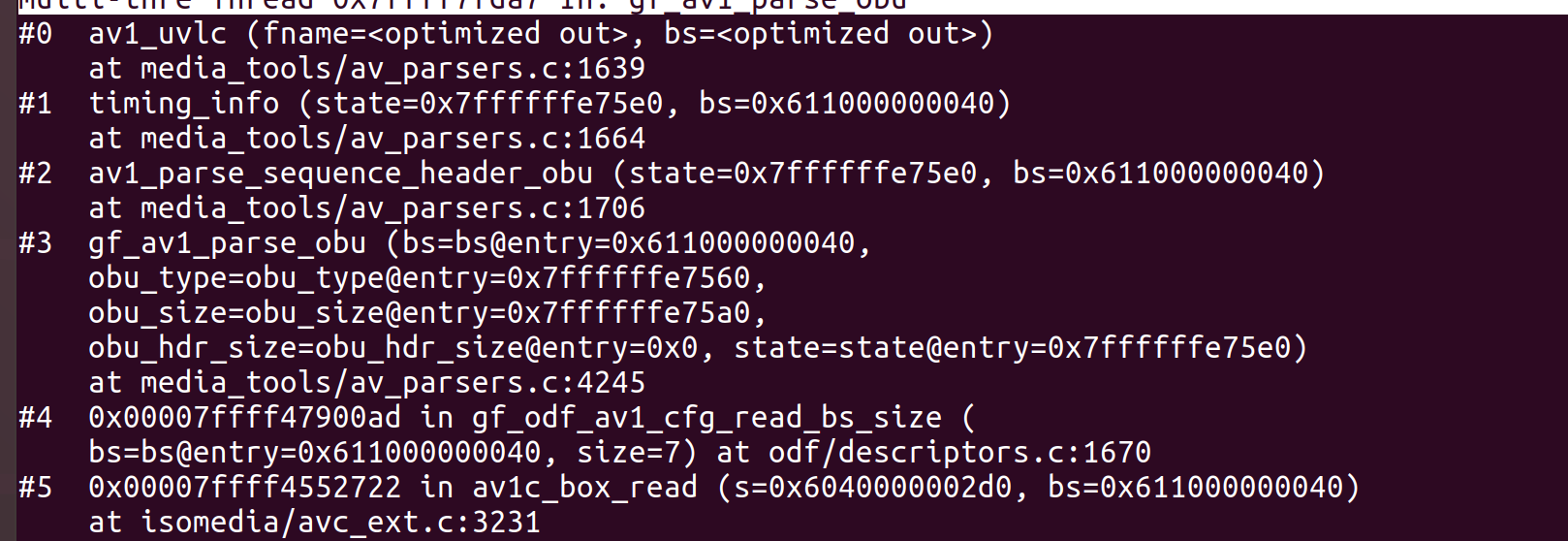
先看无限循环的地方在av_parsers.c:1639处。
gf_bs_read_int函数的两个参数第一个为bitstream,第二个为读取的Bits数,函数为从bitsteam读取1Bits为int值返回。
此时传参如下,bitstream为0x611000000040,读取1Bits。
进入函数,此时已经读了6052068字节。
整个循环就是已经读到了stream结尾但是一直还在继续读取字节。可以发现bs的size和position都是507(0x1FB),而我们的文件大小就是0x1FB。
在此循环运行的第一次打断点。
发现current为0x4A00的值,像是读取到了文件末尾的4A自动补充了一个00。
至此漏洞点是大概清楚了,就是读完了文件还在继续读。
0x03 报告
1.Version
MP4Box - GPAC version 2.3-DEV-rev636-gfbd7e13aa-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - https://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-bin --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2.Program Output
[iso file] Parsing a top-level box at position 0
[iso file] Read Box type ftyp size 32 start 0
[iso file] Parsing a top-level box at position 32
[iso file] Read Box type mv@d size 108 start 32
[iso file] Unknown top-level box type mv@d
[iso file] Parsing a top-level box at position 140
[iso file] Read Box type av1C size 363 start 140
[AV1] parsed AV1 OBU type=7 size=99 at position 152.
[AV1] AV1 unexpected OBU type=152 size=0 found at position 140056310360544. Forwarding.
[AV1] parsed AV1 OBU type=1 size=12 at position 251.
[AV1] parsed AV1 OBU type=1 size=12 at position 263.
[AV1] parsed AV1 OBU type=1 size=12 at position 275.
[AV1] parsed AV1 OBU type=1 size=12 at position 287.
[AV1] parsed AV1 OBU type=2 size=25 at position 299.
[AV1] AV1 unexpected OBU type=299 size=0 found at position 140056310360544. Forwarding.
[AV1] parsed AV1 OBU type=2 size=52 at position 324.
[AV1] AV1 unexpected OBU type=324 size=0 found at position 140056310360544. Forwarding.
[AV1] parsed AV1 OBU type=1 size=12 at position 376.
[AV1] parsed AV1 OBU type=1 size=12 at position 388.
[AV1] parsed AV1 OBU type=1 size=12 at position 400.
[AV1] parsed AV1 OBU type=1 size=12 at position 412.
[AV1] parsed AV1 OBU type=1 size=12 at position 424.
[AV1] parsed AV1 OBU type=1 size=12 at position 436.
[AV1] parsed AV1 OBU type=1 size=12 at position 448.
[AV1] parsed AV1 OBU type=1 size=12 at position 460.
[AV1] parsed AV1 OBU type=1 size=12 at position 472.
[AV1] parsed AV1 OBU type=1 size=12 at position 484.
[BS] Attempt to overread bitstream
3.Reproduction
./MP4Box -v $poc
4.PoC
https://www.mediafire.com/file/fspsarzrcbfceha/hangPoC/file
5.Impact
This vulnerability can result in an infinite loop or lead to a denial-of-service (DoS) condition.
6.Env
Linux ubuntu 5.4.0-84-generic #94~18.04.1-Ubuntu SMP Thu Aug 26 23:17:46 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
7.Credit
hu1y40
0x04 修复方案
其实我还想加一个是否在文件结尾的标识 不过既然leadingZeros>=32都会返回0xFFFFFFFF不如在循环中一旦发现了leadingZeros>=32就返回。
static u32 av1_uvlc(GF_BitStream *bs, const char *fname)
{
u32 res;
u8 leadingZeros = 0;
while (1) {
if (leadingZeros >= 32) {
return 0xFFFFFFFF;
}
Bool done = gf_bs_read_int(bs, 1);
if (done)
break;
leadingZeros++;
}
res = gf_bs_read_int(bs, leadingZeros) + (1 << leadingZeros) - 1;
gf_bs_log(bs, 2*leadingZeros, fname, res);
return res;
}
0x05 问题
1.对于这种价值较低的漏洞有必要分析详细吗?(此漏洞并没有分析特别详细,包括文件格式为什么如此解析,流对象等)
文章评论